Classification: – Impact : Loss of confidentiality, integrity, and availability – Exploitability : Unknown exploit – Resolution : Apply updates Affected Versions: – Firefox 136.0.4 – Firefox ESR 128.8.1 – Firefox ESR 115.21.1 Risk Assessment: – Remote code execution (RCE) allowing system compromise. Vulnerability Summary: Mozilla has patched a critical sandbox escape vulnerability in Firefox’s Inter-Process Communication (IPC) mechanism. Attackers could exploit improper handling of system handles to elevate privileges and bypass sandbox protections, potentially gaining control of affected systems. This flaw shares similarities with CVE-2025-2783, a recently exploited Chrome vulnerability. Patched Versions: – Firefox 136.0.4 – Firefox ESR 128.8.1 – Firefox ESR 115.21.1 Action Required : Immediate update to the latest version to mitigate exploitation risks. References: – CVE-2025-2857 – CVSS 3.1 Score : 9.8 (Critical) Remediation: Download the latest secure release: – [Firefox 136.0.4 Release Notes Firefox 136.0.4, See All New Features, Updates and Fixes – [Firefox ESR 115.21.1 Release Notes Firefox ESR 115.2.1, See All New Features, Updates and Fixes – [Firefox ESR 128.8.1 Release Notes Firefox ESR 128.8.1, See All New Features, Updates and Fixes Key Improvements: Stronger Structure : Clear section headers and bullet points for readability. Technical Precision : Terms like “sandbox escape” and “RCE” align with industry standards. Conciseness : Removed redundant phrasing (e.g., “It is strongly recommended” → “Action Required”). Professional Tone : Neutral yet urgent language for security advisories.
Authentication Bypass Vulnerability in VMware Tools for Windows
Classification: Impact: Loss of confidentiality: An attacker can access sensitive information without authorization. Loss of integrity: Potential modification of critical data or configurations. Loss of availability: Possible disruption of affected services. Exploit: As of now, no known public exploits have been reported. Solution: Update to a patched version is recommended. Affected Systems: VMware Tools versions 12.x.x and 11.x.x on Windows. Risks: Privilege escalation : A non-administrative user could execute commands with elevated privileges, compromising system security. Authentication bypass : An attacker could access normally protected resources without providing valid credentials. Vulnerability Summary A critical vulnerability, identified as CVE-2025-22230, has been discovered in VMware Tools for Windows. This flaw allows an attacker with non-administrative privileges on a Windows virtual machine to bypass authentication mechanisms and execute commands with elevated privileges. Exploiting this vulnerability could enable an attacker to: Access sensitive data stored on the virtual machine. Alter or delete system files and configurations. Disable certain security mechanisms, thereby compromising system integrity. Prepare for more advanced attacks, such as establishing persistence or launching additional malicious actions. Severity Score and References CVE-2025-22230 CVSS 3.1 Score: 7.8 (High) CVSS Evaluation Criteria: Attack Vector : Local Attack Complexity : Low Privileges Required : Low User Interaction : None Confidentiality Impact : High Integrity Impact : High Availability Impact : High Solution and Remediation Measures Recommended update to VMware Tools version 12.5.1 (which patches the vulnerability). Actions to take: Verify the current version of VMware Tools installed on affected machines. Download and install the patched version (12.5.1) available via Broadcom. Implement additional security measures by restricting user privileges on virtual machines. Monitor activity logs to detect any attempts to exploit this vulnerability. Official Update and Information Link:https://support.broadcom.com/web/ecx/support-content-notification/-/external/content/SecurityAdvisories/0/25518Broadcom Advisory This update is mandatory to ensure the security of virtualized environments using VMware Tools on Windows.
Security Bulletin: Critical Vulnerabilities in Microsoft Edge
General Information – Affected Product : Microsoft Edge – Publication Date : March 24, 2025 – Source : Microsoft Edge Security Bulletin Vulnerability Classification – Impact : – Loss of confidentiality – Loss of integrity – System unavailability – Exploitability : No known exploits at this time – Recommended Solution : Update to the latest version of Microsoft Edge Affected Systems The following versions of Microsoft Edge are affected by these vulnerabilities: – Microsoft Edge (Chromium-based) : Versions 134.0.6998.117/118 and earlier – Microsoft Edge : Version 134.0.3124.83 and earlier Users and administrators must ensure their browser is up to date to prevent exploitation of these vulnerabilities. Security Risks and Impacts Exploitation of the identified vulnerabilities may lead to the following major risks: Arbitrary Code Execution : An attacker could remotely execute malicious code on the affected system, compromising data integrity and confidentiality. Privilege Escalation : A malicious user could exploit a flaw to gain higher privileges than intended, enabling partial or full system control. Use-After-Free Memory Corruption : This vulnerability may lead to memory corruption, causing browser crashes or facilitating the execution of malicious code. Vulnerability Details: Several vulnerabilities have been identified and assigned the following CVE codes: – CVE-2025-29795 : – CVSS 3.1 Score : 7.8 (High) – Type : Privilege Escalation – Description : A flaw allows an attacker to elevate privileges by exploiting a weakness in the browser’s rendering engine. – CVE-2025-2476 : – CVSS 3.1 Score : 9.8 (Critical) – Type : Use-After-Free – Description : Improper memory management could be exploited by an attacker to execute arbitrary code or crash the browser. – CVE-2025-29806: – CVSS 3.1 Score : 6.5 (Medium) – Type : Arbitrary Code Execution – Description : A vulnerability allows an attacker to execute remote code by tricking a user into visiting a malicious website. Solutions and Patches Microsoft has released security patches to address these vulnerabilities. It is strongly recommended to apply these updates as soon as possible. Patches are available at the following links: Correctif CVE-2025-29795 Correctif CVE-2025-2476 Correctif CVE-2025-29806 Recommendations To mitigate risks associated with these vulnerabilities, users and administrators are advised to: Update Microsoft Edge by downloading the latest available version. Enable automatic updates to ensure the browser remains protected against new threats. Avoid opening suspicious links sent via email or displayed on untrusted websites. Strengthen system security by following cybersecurity best practices. Conclusion The vulnerabilities discovered in Microsoft Edge pose a critical risk to user security. Exploitation could allow an attacker to execute arbitrary code, escalate privileges, or compromise system memory. Applying patches and maintaining a secure environment are essential to mitigating these threats.
Red Hat OpenShift Container Platform Vulnerability
Creation Date : March 21, 2025 Source : Red Hat Security Bulletin Classification : Impact: Loss of confidentiality Exploit: Unknown exploit Solution: Unknown solution Product Status: Vendor Product Version Red Hat OpenShift 4 Conclusion A vulnerability of medium severity has been identified in the OpenShift console at the /locales/resources.json endpoint, which is used to provide multilingual resources via plugins. The lng and ns parameters are insecurely handled in the code (pkg/plugins/handles/unsafely.go #L112) for generating file paths. This flaw allows an authenticated user to manipulate these parameters using sequences like ../ to access any JSON file on the console pod via a directory traversal attack. References: CVE-2024-7631 CVSS Score: 4.30 CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N (Vector String) Red Hat Bugzilla: https://bugzilla.redhat.com/show_bug.cgi?id=2296053 Vendor-Specific Advisory URL: https://access.redhat.com/security/cve/cve-2024-7631 Mitigation: Currently, Red Hat does not recommend mitigation measures. Please update to a patched version of the component as soon as it becomes available.
Remote Code Execution Vulnerability in Microsoft Dataverse
Creation Date : March 21, 2025 Source : Microsoft Security Bulletin ———————————————————————– Classification: – Impact : Loss of confidentiality, integrity – Exploit : Unknown exploit – Solution : Update Product Status: Vendor : Microsoft Product :Microsoft Dataverse Platforms :Unknown Conclusion: The discovery of a remote code execution vulnerability in Microsoft Dataverse highlights the ongoing challenges in maintaining cybersecurity in complex software systems. This vulnerability, caused by the deserialization of untrusted data, posed significant risks, including potential unauthorized code execution by attackers. However, Microsoft has promptly addressed the issue, releasing a patch to mitigate the threat. Users of Microsoft Dataverse are advised to ensure their systems are up to date, although no additional action is required as the fix has been automatically applied. This incident underscores the importance of proactive security measures, regular updates, and the need for organizations to stay informed about potential vulnerabilities in their software ecosystems. By leveraging resources like the Microsoft Security Advisory and adhering to best practices, businesses can better protect their data and infrastructure from emerging threats. For more details, refer to the official Microsoft Security Advisory: [CVE-2025-29807](https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-29807). References: – CVE-2025-29807 – CVSS score 8.7 – CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:H/I:H/A:N/E:U/RL:O/RC:C (Vector String) Microsoft Security Advisory: – Security Update Guide – Microsoft Security Response Center Solution: – This vulnerability has already been patched by Microsoft. Users of the service do not need to take any action. CVE-2025-29807 – Security Update Guide – Microsoft – Microsoft Dataverse Remote Code Execution Vulnerability
SMB Protocol (Server Message Block) on Windows Server 2022
The enhancements to the SMB (Server Message Block) protocol on Windows Server 2022 and Windows 11 bring several significant improvements in terms of performance, security, and resource management. Here are some of the key enhancements: Enhanced Performance SMB Direct : Windows Server 2022 and Windows 11 support SMB Direct, which enables high-speed, low-latency communication using RDMA (Remote Direct Memory Access) network cards. This is particularly useful for environments requiring fast data transfers, such as databases or virtualized applications. Improved SMB Compression : SMB compression has been optimized to reduce the size of data transferred over the network, which can improve performance, especially on bandwidth-constrained networks. Enhanced Security SMB AES-128-GCM and AES-128-CCM : Windows Server 2022 and Windows 11 support AES-128-GCM and AES-128-CCM encryption for SMB, providing enhanced security while reducing processing overhead compared to AES-128-CCM. SMB over QUIC Support : SMB over QUIC allows secure access to shared files over the internet without the need for a VPN. QUIC is a modern transport protocol that offers better performance and security compared to traditional protocols like TCP. Improved Resource Management Enhanced SMB Multichannel : SMB Multichannel allows the use of multiple network connections simultaneously to increase throughput and redundancy. The improvements in Windows Server 2022 and Windows 11 enable better network resource management and more efficient load balancing. SMB Bandwidth Control : It is now possible to configure bandwidth limits for SMB connections, allowing for better network resource management and preventing network congestion. Compatibility and Interoperability Extended Support for SMB 3.1.1 : Windows Server 2022 and Windows 11 support version 3.1.1 of the SMB protocol, which includes improvements in security and performance. This version is also backward compatible with older versions of SMB, ensuring interoperability with legacy systems. Enhancements for Virtualized Environments SMB for Virtual Machines : The improvements to SMB in Windows Server 2022 and Windows 11 are particularly beneficial for virtualized environments, where the performance and security of data transfers are critical. Monitoring and Diagnostics Improved Diagnostic Tools : Windows Server 2022 and Windows 11 include enhanced diagnostic tools for monitoring and troubleshooting SMB-related issues, making it easier to manage and troubleshoot file shares. in conclusion, the enhancements to SMB on Windows Server 2022 and Windows 11 aim to provide better performance, enhanced security, and more efficient network resource management, while ensuring compatibility with existing systems. These advancements are particularly beneficial for enterprise environments and virtualized infrastructures.
Vulnerability (Use-after-Free) in Google Chrome
Google has deployed a crucial security update to address a critical use-after-free vulnerability in the Lens feature of Google, tracked under the name CVE-2025-2476. Exploiting this flaw could allow an attacker to execute arbitrary code or potentially take control of a system Creation Date: 20 March 2025 Source : Google Chrome Security Bulletin Classification: Impact: Loss of confidentiality, integrity, availability Exploit: Unknown exploit Solution: Update Affected Systems: Google Chrome Version 134.0.6998.118 (For Windows and Mac) Google Chrome Version 134.0.6998.117 (For Linux) Summary: Google has deployed a crucial security update to address a critical use-after-free vulnerability in the Lens feature of Google, tracked under the name CVE-2025-2476. Exploiting this flaw could allow an attacker to execute arbitrary code or potentially take control of a system. References: CVE-2025-2476 CVSS score 9.80 Google Security Advisory: Chrome Releases: Stable Channel Update forDesktop Solution: Google Chrome Version 134.0.6998.118 (For Windows and Mac).https://www.google.com/chrome/ Google Chrome Version 134.0.6998.117 (For Linux). https://www.google.com/chrome/
Vulnérabilités affectant Microsoft Windows Server
Description: Microsoft has announced the patching of several vulnerabilities affecting the aforementioned versions of its Windows operating system. Many of these vulnerabilities are zero-days that are likely being actively exploited. Exploiting these vulnerabilities could allow an attacker to escalate privileges, execute arbitrary code, access confidential data, or bypass security measures. Severity: High Classification: Location: Physical access required / Local / Remote Impact: Loss of confidentiality, loss of integrity, loss of availability Exploit: (Exploit unknown) Disclosure: Verified by the vendor Affected Systems: Windows Server 2025 (Server Core installation) Windows Server 2025 Windows Server 2022, 23H2 Edition (Server Core installation) Windows Server 2022 (Server Core installation) Windows Server 2022 Windows Server 2019 (Server Core installation) Windows Server 2019 Windows Server 2016 (Server Core installation) Windows Server 2016 Windows Server 2012 R2 (Server Core installation) Windows Server 2012 R2 Windows Server 2012 (Server Core installation) Windows Server 2012 Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) Windows Server 2008 for x64-based Systems Service Pack 2 Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation) Windows Server 2008 for 32-bit Systems Service Pack 2 Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) Windows Server 2008 R2 for x64-based Systems Service Pack 1 Patch de sécurité : Windows Server 2012 R2 (Monthly Rollup) Link : https://catalog.update.microsoft.com/v7/site/Search.aspx?q=KB5053887. Windows Server 2012 (Monthly Rollup) Link: https://catalog.update.microsoft.com/Search.aspx?q=KB5053886 Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Monthly Rollup) Link : https://catalog.update.microsoft.com/Search.aspx?q=KB5053620 Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Security Only) Link : https://catalog.update.microsoft.com/Search.aspx?q=KB5053627 Windows Server 2008 for x64-based Systems Service Pack 2 (Monthly Rollup) Link : https://catalog.update.microsoft.com/Search.aspx?q=KB5053888 Windows Server 2008 for x64-based Systems Service Pack 2 (Security Only)** Link : https://catalog.update.microsoft.com/Search.aspx?q=KB5053995 Windows Server 2008 for 32-bit Systems Service Pack 2 (Monthly Rollup)** Link : https://catalog.update.microsoft.com/Search.aspx?q=KB5053888 Windows Server 2008 for 32-bit Systems Service Pack 2 (Security Only) Link : https://catalog.update.microsoft.com/Search.aspx?q=KB5053995 Windows Server 2016 Link : https://catalog.update.microsoft.com/Search.aspx?q=KB5053594 Windows Server 2022 Link: https://catalog.update.microsoft.com/Search.aspx?q=KB5053603 Windows Server 2019 Link : https://catalog.update.microsoft.com/Search.aspx?q=KB5053596 Windows Server 2025 Link : https://catalog.update.microsoft.com/Search.aspx?q=KB5053598 Windows Server 2022, 23H2 Edition (Server Core installation) Link : https://catalog.update.microsoft.com/Search.aspx?q=KB5053599 CVE References: Microsoft Security Bulletin Windows https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-9157 Microsoft Security Bulletin Windows CVE-2025-21180 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-21180 Microsoft Security Bulletin Windows CVE-2025-21247 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-21247 Microsoft Security Bulletin Windows CVE-2025-24035 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24035 Microsoft Security Bulletin Windows CVE-2025-24044 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24044 Microsoft Security Bulletin Windows CVE-2025-24045 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24045 Microsoft Security Bulletin Windows CVE-2025-24046 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24046 Microsoft Security Bulletin Windows CVE-2025-24048 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24048 Microsoft Security Bulletin Windows CVE-2025-24050 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24050 Microsoft Security Bulletin Windows CVE-2025-24051 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24051 Microsoft Security Bulletin Windows CVE-2025-24054 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24054 Microsoft Security Bulletin Windows CVE-2025-24055 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24055 Microsoft Security Bulletin Windows CVE-2025-24056 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24056 Microsoft Security Bulletin Windows CVE-2025-24059 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24059 Microsoft Security Bulletin Windows CVE-2025-24061 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24061 Microsoft Security Bulletin Windows CVE-2025-24064 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24064 Microsoft Security Bulletin Windows CVE-2025-24066 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24066 Microsoft Security Bulletin Windows CVE-2025-24067 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24067 Microsoft Security Bulletin Windows CVE-2025-24071 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24071 Microsoft Security Bulletin Windows CVE-2025-24072 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24072 Microsoft Security Bulletin Windows CVE-2025-24076 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24076 Microsoft Security Bulletin Windows CVE-2025-24084 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24084 Microsoft Security Bulletin Windows CVE-2025-24983 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24983 Microsoft Security Bulletin Windows CVE-2025-24984 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24984 Microsoft Security Bulletin Windows CVE-2025-24985 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24985 Microsoft Security Bulletin Windows CVE-2025-24987 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24987 Microsoft Security Bulletin Windows CVE-2025-24988 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24988 Microsoft Security Bulletin Windows CVE-2025-24991 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24991 Microsoft Security Bulletin Windows CVE-2025-24992 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24992 Microsoft Security Bulletin Windows CVE-2025-24993 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24993 Microsoft Security Bulletin Windows CVE-2025-24994 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24994 Microsoft Security Bulletin Windows CVE-2025-24995 :https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24995 Microsoft Security Bulletin Windows CVE-2025-24996 du 11 mars 2025 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24996 Microsoft Security Bulletin Windows CVE-2025-24997 du 11 mars 2025 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24997 Microsoft Security Bulletin Windows CVE-2025-25008 du 11 mars 2025 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-25008 Microsoft Security Bulletin Windows CVE-2025-26633 du 11 mars 2025 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-26633 Microsoft Security Bulletin Windows CVE-2025-26634 du 11 mars 2025 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-26634 Microsoft Security Bulletin Windows CVE-2025-26645 du 11 mars 2025 https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-26645 CVE References CVE-2024-9157 : https://www.cve.org/CVERecord?id=CVE-2024-9157 CVE-2025-21180 https://www.cve.org/CVERecord?id=CVE-2025-21180 CVE-2025-21247 https://www.cve.org/CVERecord?id=CVE-2025-21247 CVE-2025-24035 https://www.cve.org/CVERecord?id=CVE-2025-24035 CVE-2025-24044 https://www.cve.org/CVERecord?id=CVE-2025-24044 CVE-2025-24045 https://www.cve.org/CVERecord?id=CVE-2025-24045 CVE-2025-24046 https://www.cve.org/CVERecord?id=CVE-2025-24046 CVE-2025-24048 https://www.cve.org/CVERecord?id=CVE-2025-24048 CVE-2025-24050 https://www.cve.org/CVERecord?id=CVE-2025-24050 CVE-2025-24051 https://www.cve.org/CVERecord?id=CVE-2025-24051 CVE-2025-24054 https://www.cve.org/CVERecord?id=CVE-2025-24054 CVE-2025-24055 https://www.cve.org/CVERecord?id=CVE-2025-24055 CVE-2025-24056 https://www.cve.org/CVERecord?id=CVE-2025-24056 CVE-2025-24059 https://www.cve.org/CVERecord?id=CVE-2025-24059 CVE-2025-24061 https://www.cve.org/CVERecord?id=CVE-2025-24061 CVE-2025-24064 https://www.cve.org/CVERecord?id=CVE-2025-24064 CVE-2025-24066 https://www.cve.org/CVERecord?id=CVE-2025-24066 CVE-2025-24067 https://www.cve.org/CVERecord?id=CVE-2025-24067 CVE-2025-24071 https://www.cve.org/CVERecord?id=CVE-2025-24071 CVE-2025-24072 https://www.cve.org/CVERecord?id=CVE-2025-24072 CVE-2025-24076 https://www.cve.org/CVERecord?id=CVE-2025-24076 CVE-2025-24084 https://www.cve.org/CVERecord?id=CVE-2025-24084 CVE-2025-24983 https://www.cve.org/CVERecord?id=CVE-2025-24983 CVE-2025-24984 https://www.cve.org/CVERecord?id=CVE-2025-24984 CVE-2025-24985 https://www.cve.org/CVERecord?id=CVE-2025-24985 CVE-2025-24987 https://www.cve.org/CVERecord?id=CVE-2025-24987 CVE-2025-24988 https://www.cve.org/CVERecord?id=CVE-2025-24988 CVE-2025-24991 https://www.cve.org/CVERecord?id=CVE-2025-24991 CVE-2025-24992 https://www.cve.org/CVERecord?id=CVE-2025-24992 CVE-2025-24993 https://www.cve.org/CVERecord?id=CVE-2025-24993 CVE-2025-24994 https://www.cve.org/CVERecord?id=CVE-2025-24994 CVE-2025-24995 https://www.cve.org/CVERecord?id=CVE-2025-24995 CVE-2025-24996 https://www.cve.org/CVERecord?id=CVE-2025-24996 CVE-2025-24997 https://www.cve.org/CVERecord?id=CVE-2025-24997 CVE-2025-25008 https://www.cve.org/CVERecord?id=CVE-2025-25008 CVE-2025-26633 https://www.cve.org/CVERecord?id=CVE-2025-26633 CVE-2025-26634 https://www.cve.org/CVERecord?id=CVE-2025-26634 CVE-2025-26645 https://www.cve.org/CVERecord?id=CVE-2025-26645
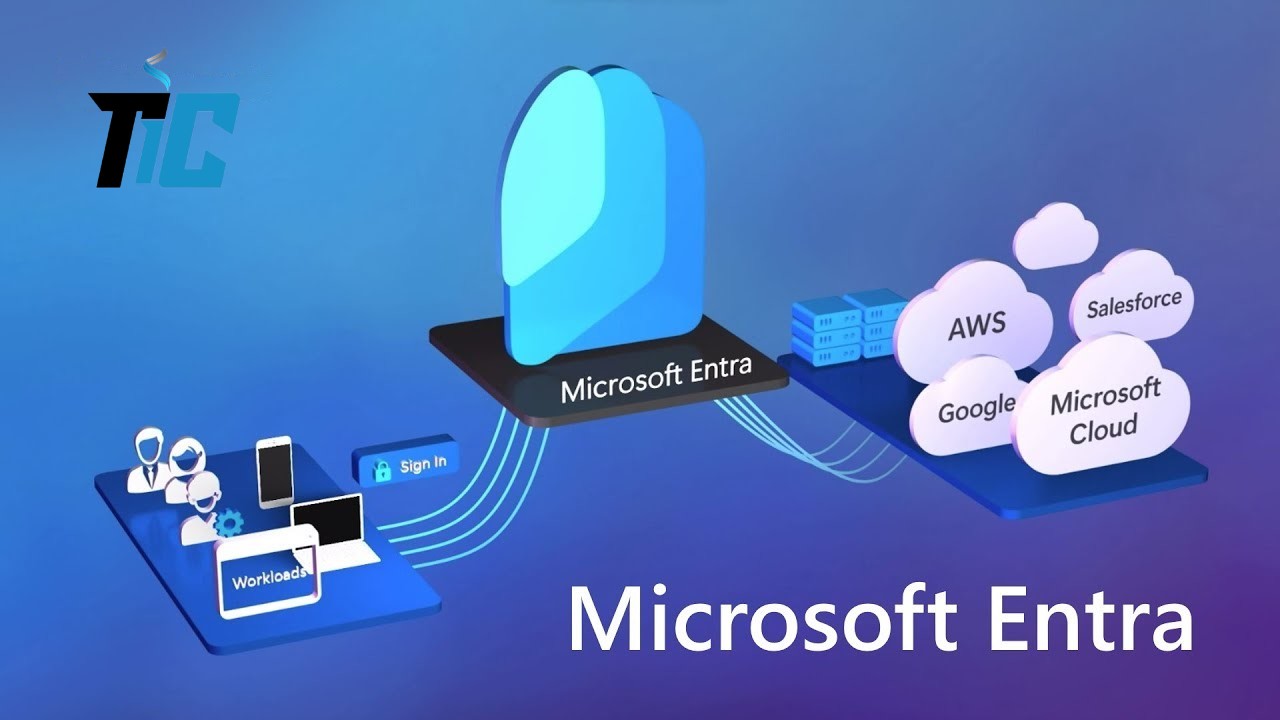
What is Microsoft Entra ID?
In today’s digital-first world, managing identities and securing access to resources is more critical than ever. But how can businesses ensure seamless and secure access across hybrid and multi-cloud environments? Enter Microsoft Entra ID, a cutting-edge identity and access management (IAM) solution designed to simplify and secure how users interact with digital resources. In this blog post, we’ll dive deep into what Microsoft Entra ID is, its key features, and why it’s a game-changer for modern enterprises. Introduction Have you ever wondered how businesses manage thousands of user identities while ensuring robust security and compliance? With the rise of remote work and cloud computing, traditional identity management systems are no longer sufficient. Microsoft Entra ID is a cloud-based IAM solution that helps organizations manage user identities, secure access to resources, and streamline authentication processes. But what makes it stand out, and how can it benefit your business? Let’s explore. The Prerequisites for Using Microsoft Entra ID Before diving into the technical details, here’s what you need to get started with Microsoft Entra ID: A Microsoft 365 or Azure subscription: Entra ID is often included in these plans. A cloud or hybrid infrastructure: Entra ID works seamlessly in both cloud and on-premises environments. Active users: You’ll need a list of users to manage within the system. Compatible devices: Entra ID supports a wide range of devices, including smartphones, tablets, and computers. Key Features of Microsoft Entra ID (H3) Centralized Identity Management Microsoft Entra ID allows businesses to manage user identities in one place, whether they’re employees, partners, or customers. This includes creating, modifying, and deleting user accounts. Multi-Factor Authentication (MFA) To enhance security, Entra ID offers multi-factor authentication, which requires users to provide two or more verification methods before accessing resources. Conditional Access Conditional access policies enable organizations to set specific rules for accessing resources. For example, you can restrict access to certain applications if a user logs in from an untrusted network. Seamless SaaS Integration Entra ID integrates with thousands of SaaS applications, making it easy for users to access their tools with a single sign-on (SSO). Technical Advantages of Microsoft Entra ID Enhanced Security: With features like MFA and conditional access, Entra ID provides robust protection against cyber threats. Simplified User Experience: Users can access all their applications with a single login, reducing password fatigue. Scalability: Whether you have 10 or 10,000 users, Entra ID scales to meet your needs. Regulatory Compliance: Entra ID helps businesses comply with regulations like GDPR by offering tools for consent management and auditing. Technical Tips for Maximizing Microsoft Entra ID Enable Multi-Factor Authentication (MFA): Activate MFA for all users to minimize the risk of unauthorized access. Set Up Conditional Access Policies: Define strict rules for accessing sensitive resources. Train Your Users: Ensure your employees understand how to use Entra ID securely. Common Mistakes to Avoid Neglecting Conditional Access: Without strict access policies, your system remains vulnerable. Ignoring Security Updates: Always keep Entra ID updated to benefit from the latest security features. Skipping User Training: Poor user practices can compromise your entire security system. Conclusion Microsoft Entra ID is more than just an identity management tool—it’s a comprehensive solution that offers security, simplicity, and scalability for businesses of all sizes. Whether you’re a small business or a large enterprise, Entra ID can help you secure your resources while providing a seamless user experience. Call-to-Action: Ready to explore Microsoft Entra ID for your business? Try it today and share your thoughts in the comments below. Don’t forget to subscribe to our blog for more insights on Microsoft technologies and best practices in identity management. FAQs Is Microsoft Entra ID free? Entra ID offers a free version with basic features, but premium plans are available for businesses with advanced needs. Can I use Entra ID with non-Microsoft applications? Yes, Entra ID integrates with thousands of third-party SaaS applications. How do I set up Multi-Factor Authentication (MFA)? You can enable MFA through the Azure portal by following the configuration steps in the “Security” section. Is Entra ID suitable for small businesses? Absolutely! Entra ID is designed to cater to businesses of all sizes, from startups to large enterprises. What’s the difference between Entra ID and Active Directory? Active Directory is primarily designed for on-premises environments, while Entra ID is a cloud-native solution with modern features like MFA and conditional access. In summary, Microsoft Entra ID is a powerful tool for securing and simplifying identity management in an increasingly digital world. Whether you’re new to IAM or an experienced IT professional, this platform offers solutions tailored to your needs. So, why not give it a try today?