Blog
Windows 10 End of Support: What You Need to Know Before October 14, 2025
Microsoft has officially announced that Windows 10 will reach end of support on October 14, 2025**. This means no more ...
Multiple Vulnerabilities in Apple Products
Classification: Impact: Loss of confidentiality, integrity, availability Exploit: Unknown exploit Solution: Update Affected Systems: iOS versions prior to 18.4.1 iPadOS ...
Multiple Vulnerabilities in Google Chrome
Creation Date | April 16, 2025Source Google | Chrome Security BulletinClassification:Impact: Loss of confidentiality, integrity, availabilityExploit: Unknown exploitSolution: UpdateAffected Systems:Chrome ...
Memory Corruption Vulnerability in Mozilla Firefox
Creation DateApril 15, 2025SourceGoogle Chrome Security BulletinClassification:Impact: Loss of confidentiality, integrity, availabilityExploit: Unknown exploitSolution: UpdateAffected Systems:Firefox versions Prior to 137.0.2Conclusion:The vulnerability CVE-2025-3608 involves ...
Content Spoofing Vulnerability in MIT Kerberos
Title: MIT KerberosCreation Date: March 24, 2025Source: Red Hat Security BulletinClassification:Impact: Loss of integrityExploit: UnknownSolution: UnknownAffected Systems:Red Hat Ansible Automation ...
Multiple Vulnerabilities in Microsoft Azure
Multiple Vulnerabilities in Microsoft Azure Date Created : 04/09/2025Source: Microsoft Azure Security BulletinClassification:Impact: Loss of integrity, confidentiality, availabilityExploit: UnknownSolution: PatchRISKS:Compromised ...
Critical BentoML Vulnerability Enables Remote Code Execution (RCE) – Exploit Available
Vulnerability Identification CVE Reference: CVE-2025-27520 CVSS Score: 9.8 (Critical) Impact: Remote Code Execution (RCE) compromising integrity, confidentiality, and availability Affected ...
Apple Security Alert 2024: Critical Vulnerabilities Found – Update Now!
Critical Apple Security Vulnerabilities: What You Need to KnowClassification:Impact: Loss of confidentiality, integrity, and availabilityExploit: Unknown exploitSolution: UpdateAffected Systems:iOS versions prior to 15.8.4iOS ...
What You Need To Know a Critical Vulnerabilities In Splunk ?
Splunk recently issued a security advisory detailing multiple high-severity vulnerabilities affecting Splunk Enterprise, Splunk Cloud Platform, and Splunk Secure Gateway. These vulnerabilities pose ...
Simplify AD User Creation: GUI & PowerShell
Active Directory (AD) is a crucial component for managing users and resources in an enterprise environment. In this guide, we ...
Critical Vulnerability in Mozilla Firefox
Classification:- Impact : Loss of confidentiality, integrity, and availability - Exploitability : Unknown exploit - Resolution : Apply updates Affected Versions:- Firefox 136.0.4 - ...
Authentication Bypass Vulnerability in VMware Tools for Windows
Classification:Impact:Loss of confidentiality: An attacker can access sensitive information without authorization.Loss of integrity: Potential modification of critical data or configurations.Loss ...
Introduction to Installing Microsoft Exchange Server 2019 via Command Line
Installing Microsoft Exchange Server 2019 might seem daunting, but by following a step-by-step approach, you can simplify the process. Using ...
Security Bulletin: Critical Vulnerabilities in Microsoft Edge
General Information - Affected Product : Microsoft Edge - Publication Date : March 24, 2025 - Source : Microsoft Edge Security Bulletin Vulnerability ...
How to Create Organizational Units (OUs) in Active Directory: GUI & PowerShell
IntroductionOrganizational Units (OUs) in Active Directory help manage users, computers, and policies efficiently. In this tutorial, we will demonstrate how ...
Red Hat OpenShift Container Platform Vulnerability
Creation Date : March 21, 2025Source : Red Hat Security BulletinClassification :Impact: Loss of confidentialityExploit: Unknown exploitSolution: Unknown solutionProduct Status:Vendor Product ...
Domain controller installation with Power Shell
Installing Active Directory using PowerShell involves several steps, including installing the necessary Windows features and promoting the server to a ...
Remote Code Execution Vulnerability in Microsoft Dataverse
Creation Date : March 21, 2025 Source : Microsoft Security Bulletin -----------------------------------------------------------------------Classification:- Impact : Loss of confidentiality, integrity- Exploit : ...
SMB Protocol (Server Message Block) on Windows Server 2022
The enhancements to the SMB (Server Message Block) protocol on Windows Server 2022 and Windows 11 bring several significant improvements ...
Vulnerability (Use-after-Free) in Google Chrome
Google has deployed a crucial security update to address a critical use-after-free vulnerability in the Lens feature of Google, tracked under ...
Vulnérabilités affectant Microsoft Windows Server
Description:Microsoft has announced the patching of several vulnerabilities affecting the aforementioned versions of its Windows operating system. Many of these ...
A vulnerability in Microsoft Windows File Explorer allows for network identity spoofing attacks: PoC published.
A critical vulnerability in Windows File Explorer has been discovered, enabling attackers to capture NTLM hashes and potentially exploit them ...
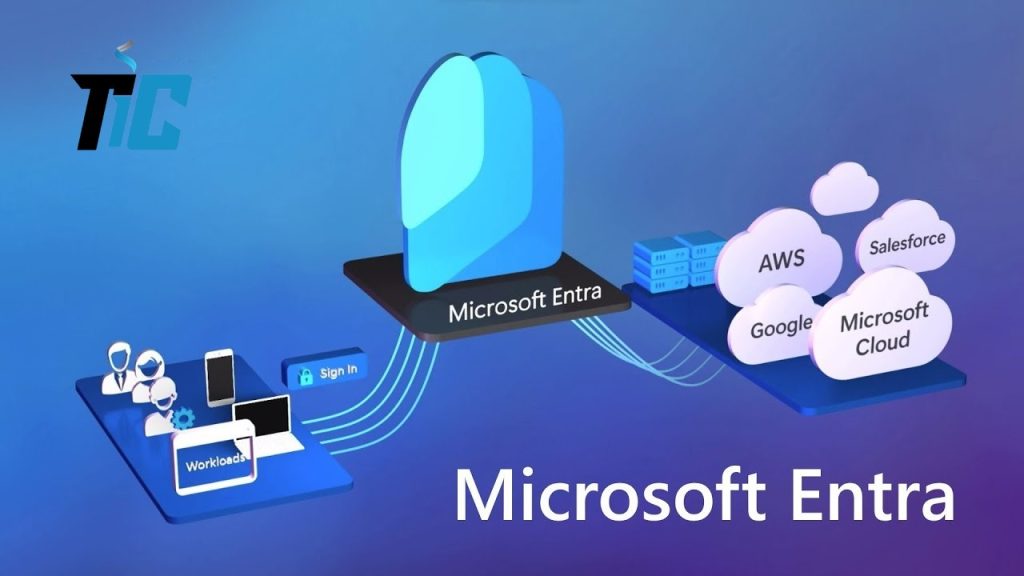
What is Microsoft Entra ID?
In today’s digital-first world, managing identities and securing access to resources is more critical than ever. But how can businesses ...
Installing and configuring an Active Directory (AD) Primary and Secondary Domain Controller
IntroductionThis guide provides a detailed step-by-step process for setting up an Active Directory (AD) environment with two domain controllers (DCs) ...
Securing Your Data: How to Prevent OneDrive Integration with ChatGPT
Nowadays, AI tools like ChatGPT play a major role in optimizing work and improving productivity. However, when it comes to ...
Multiple Vulnerabilities in Microsoft Azure
Multiple Vulnerabilities in Microsoft Azure Reference : Theitcommunity.com Title : Vulnerabilities in Multiple Microsoft Azure Components Date Created : March ...
Microsoft’s March 2025 Patch Tuesday
We would like to inform you that Microsoft has released the March 2025 Patch Tuesday addressing various Microsoft components and solutions. This ...
Cloud Computing: Why It’s the Best Choice for Startups
Cloud computing can be classified into several types based on the service model and deployment model. Here is a view ...
Replacing Remote Desktop with Windows App: How to Get Started!
Are you still relying on traditional remote desktop solutions to access your work or personal files from afar? In a ...
Types of Cloud Computing Based on Deployment Models
Public CloudWhat it is: Public clouds are owned and operated by third-party cloud service providers like Amazon Web Services (AWS), Microsoft Azure, ...
Understanding DNS: The Backbone of the Internet
The Domain Name System (DNS) is one of the most critical components of the internet, yet it often operates behind ...
How To Create new tenant Azure Cloud?
To create an Azure Cloud tenant, follow these steps: Go To portal azure Go To Manage Entra ID click on View ...